Is in that location a mode to hack into someone'due south telephone without them knowing?
The answer is yes, and it no longer takes a tech genius to make this happen.
TechCrunch recently discovered a security issue that puts thousands of people's private telephone information at risk. And it all points to spyware that anyone can access. Worse nonetheless, information technology has become easier than e'er to purchase consumer-grade software that lets you lot install "stalkerware" on someone's phone. This makes it elementary to admission someone else'southward private text messages, telephone call records, geolocation, photos, videos, and browsing history.
Learning how bad actors tin can infiltrate the device of a nonconsenting target will keep you from falling victim to the ploy.
Pro tip: Prevent spyware and other forms of malware from wreaking havoc on your telephone. A quick download of Clario, a powerful antivirus software, will spare you a lot of trouble. Follow these simple steps to equip your Android telephone with existent-time protection:
- Install Clario for Android.
- Click the First browse button to activate its Spyware detector.
- Start protecting your Android telephone today with Clario's 7-day free trial.
Now, let's talk about the various ways hackers can set on your telephone.
- How to hack into an Android phone
- How to hack someone's phone camera remotely
- How to hack someone'due south telephone with just their number
- How to protect yourself from spyware
How does hacking into an Android phone happen
Nowadays, all it takes to hack an Android telephone is a quick sign-upward with a popular spyware app and a few minutes of physical access to the target device. Government agencies and seasoned cybercriminals can easily hack into an Android phone remotely.
"Legitimate" spyware apps
People utilize spyware apps for various legitimate reasons, including parental control of a kid's phone, tracking a lost device, or keeping tabs on employee activities. However, these tools tin can also be used with malicious intent and without the target's knowledge.
So, are y'all vulnerable to such an attack? The practiced news is that spyware apps often crave physical access to your device at least once. The bad news is that if information technology happens one time, then the phone hacking tin can go along from afar. You won't fifty-fifty realize y'all're existence monitored.
Some of the most normally used apps for spying on other devices are mSpy, Spyic, and Cocospy.
Protection tips: As yous can come across, the nearly constructive way to avoid these spyware apps is by keeping your phone out of the hackers' physical attain. Don't get out it unattended, and try not to lend it to strangers.
Are you worried that someone has already infiltrated your phone? Follow these steps to manually cheque your Android phone for spyware:
- Become to Settings.
- Tap Apps and notifications and See all apps.
- Look for suspicious and unfamiliar carte items, then uninstall them.
Y'all may also rely on antivirus software to browse the Android device for you.
Spyware Trojans
Some forms of spyware are packaged as Trojans. They announced every bit harmless or even helpful pieces of software. But their goal is not harmless at all: they try to go any targets to download the spyware hiding within the Trojan. To make this happen, hackers apply social engineering tactics or psychological manipulation. For case, they may send emails promising a free giveaway to convince their targets to download a plan.
SpyNote, an Android remote access trojan (RAT), is one threat you should sentry out for. Information technology tin view text letters, access your phone's video camera, heed to sound captured past the microphone, and determine the last known GPS location. Yous may unknowingly add it to your organisation by downloading apps from 3rd-party sources outside of Google Play.
Protection tips: Armed with tools similar SpyNote, hackers don't need physical access to your telephone to create havoc. To protect your device, brand sure you only download apps from trusted sources. And don't let appearances fool yous, not when a SpyNote variant once masqueraded every bit a Netflix app.
You should too be wary of providing excessive permissions to apps. Surely, a computer app doesn't need access to your microphone or your contacts. You may too want to bank check the apps' reputation. Don't only rely on the reviews. It's best to check the identity of the developers and if they're a legitimate business.
Keep in mind that the hackers may endeavour to get to you through social applied science, and so make sure you avoid clicking on suspicious e-mail attachments or SMS links.
"Serious" spyware
You lot may accept read near Pegasus in the news. This powerful piece of spyware tin secretly admission your messages, tape your calls, and actuate your camera. It essentially turns your phone into a 24-hour surveillance device. And hackers don't even demand to bear on your phone or convince you to click on a link to infiltrate your system. All they accept to do is make a WhatsApp call to your telephone, and Pegasus will be on its way. Yous don't even have to answer it!
Now, the good news is that potent tools like Pegasus are accessible only to authorities agencies. Unless you're a announcer, homo rights activist, primary executive, or authorities official, you won't have to worry about condign a target.
Protection tips: In the rare event that you may be targeted by the regime, you can check if your device has been compromised using the Amnesty International Mobile Verification Toolkit (MVT). This tool can analyze the files and configuration of a fill-in taken from your mobile device. Even so, the MVT can only go as far equally to look for set on indicators. Information technology won't be able to tell you with certainty that your device has been infiltrated.
How does hacking someone'due south phone camera remotely happen
As we mentioned, invaders can easily hack your photographic camera from afar using solutions like SpyNote. All it takes is persuading you into clicking on a malicious link.
Spyware apps marketed for parental control besides provide cybercriminals with a handy mode to hack your camera. Popular apps similar FlexiSPY and MobileSpy provide live access to a phone camera, assuasive hackers to take videos and photos using the target device. Merely merely like with most "legitimate" spyware apps, hackers need physical access to your phone to install the malware. So, to avert such an assail, make sure you keep your phone on a leash — never mitt information technology over to people you don't trust.
How does hacking telephone with just their number happen
Governments, as we just said, can use surveillance tools similar Pegasus to tap into someone'south prison cell telephone without touching it. All it takes is a WhatsApp call. Once they get a hold of your telephone number, y'all're fair game.
Now, you may wonder if cybercriminals can exercise every bit much with just a number. German security researcher Karsten Nohl one time demonstrated to a CBS evidence a technique attackers use to hack phones. He successfully infiltrated a US congressman's phone and used it to track the statesman'south whereabouts, tape his calls, and read his messages.
This technique takes reward of the vulnerability coming with the network interchange service chosen Signalling System No. 7 (SS7), which allows different mobile phone networks to exchange data and bills correctly. The pull a fast one on requires avant-garde technical skills and is accessible only to seasoned hackers. However, information technology's best to share your phone number just when necessary. Keep it out of the public's eye.
How to protect yourself from spyware
To prevent spyware from creeping into your phone, you demand to make sure your device never falls into the wrong hands. Try to avert clicking on suspicious links, opening malicious websites, or downloading apps from unknown sources.
That said, you can do everything to protect your telephone and privacy, but some forces are but greater than your best efforts. Fortunately, you tin equip your device with cybersecurity software that will do a improve chore than you.
Follow these quick and like shooting fish in a barrel steps to protect your Android phone from spyware:
- Download and install Clario on your Android phone, and so create an business relationship.
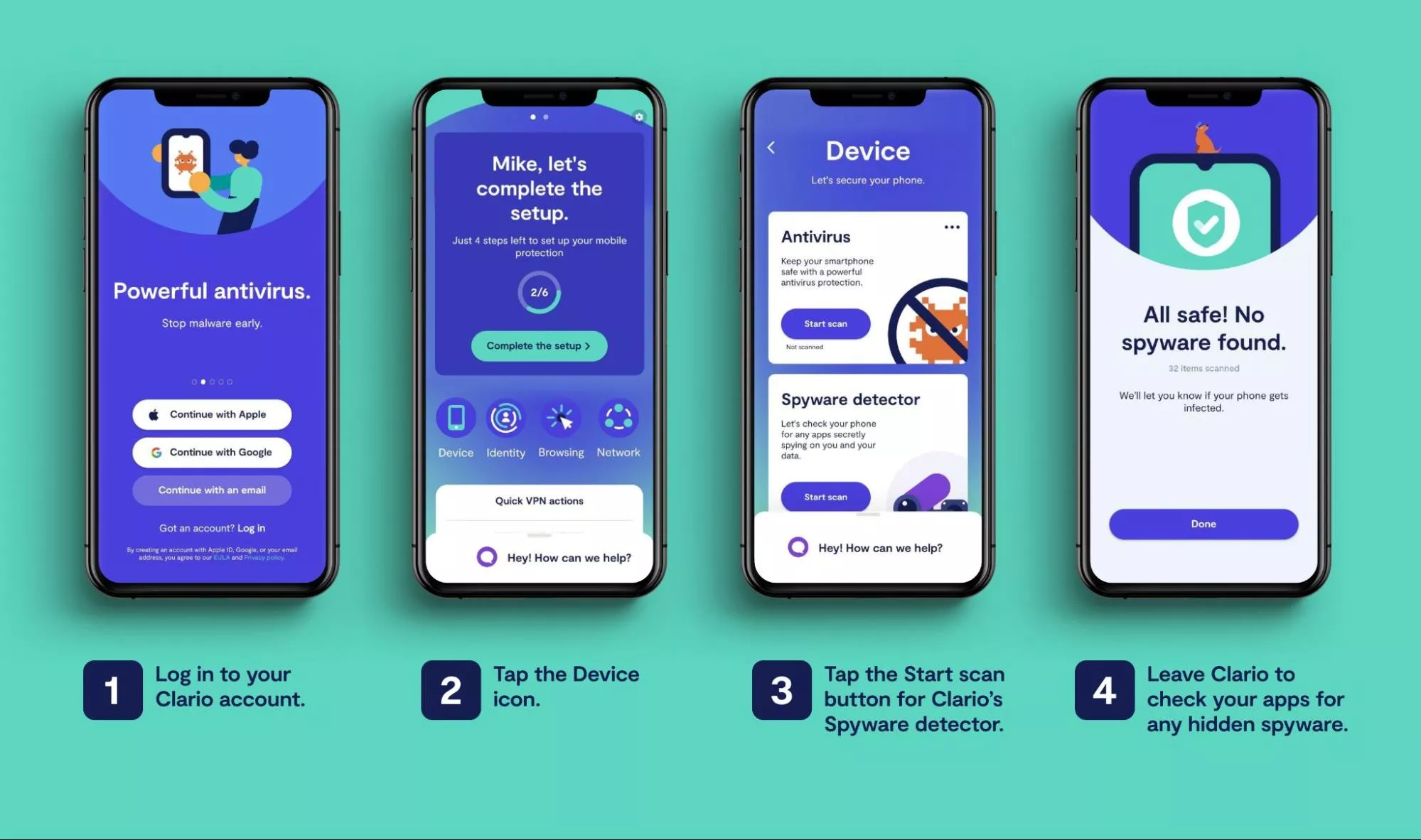
- Log in to your Clario account.
- Tap the Device icon.
- Tap the Start scan button for Clario's Spyware detector.
- Go out Clario to cheque your apps for any hidden spyware.
Clario also checks every new app for malware and informs yous if it detects a threat.
***
Someone could exist reading your WhatsApp messages, taking photos with your camera, and recording your keystrokes to effigy out your passwords — all without your knowledge! Now that we practise almost everything on our phones, this threat is more than alarming than always. Fortunately, cybersecurity software providers are fast catching upwardly with these threats. With the correct app, you get to proceed your peace of listen in this chaotic new earth.
Keep reading:
- Codes to Check If Your Phone Is Tapped
- How to Secure Your iPhone from Hackers in 9 Steps
- How to tell if your phone is hacked past someone?
- How to Remove Spyware from Your Android Phone
DOWNLOAD HERE
Posted by: youngdairriortand.blogspot.com

0 Comments